Is my Network Architecture Secure?
What type of security framework, policies and processes do I need to help secure my company better?
7/31/20253 min read


If I were to put the above question to a search engine I would get multiple types of answers. Things related to security frameworks and maybe something about NIST but will sure get a list of responses from Security vendors proposing security products from IAM to Next Gen Firewalls, to cloud security offerings such as SSE and so on. This blog attempts to discuss the topic so let’s get on with it.
When I think about security architectures multiple things come to mind from frameworks to processes to tools and products. I think a better question would be what type of Security Framework, policies and processes do I need to help secure my company better? And from there you investigate what technologies are needed but as always with everything we must first understand what’s exactly we are trying to secure.
If you visit Europe, you will get the chance to see many castles that were built with security in mind to protect kings, lords and the like. Castles had moats around them, and they were protected with a lot of firepower. We used this same model earlier in networking. The data center was our castle where we kept all the critical apps / data and anyone trying to access the data center was subjected to access controls. This model however doesn’t work in today’s world because we moved from a centralized model to a distributed model and our data and the people who are trying to access them are all spread out everywhere. Today we are in the world of Zero Trust a term that Gartner coined several years back hinting to the notion that we no longer have boundaries and every transaction between client and server for example need to be inspected.
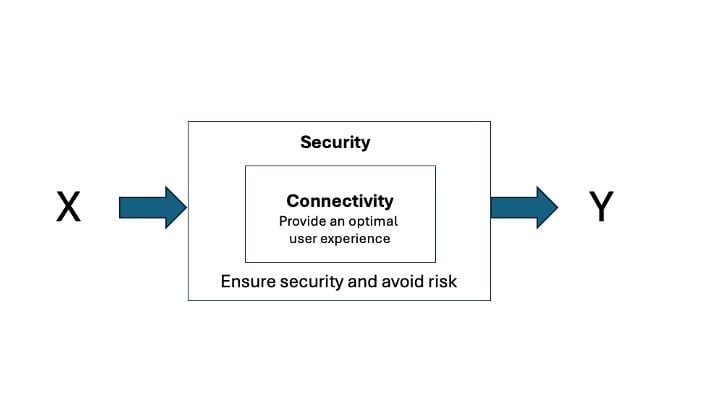
The above is clearly saying that for X to connect to Y the traffic must be subjected to inspection. What type of inspection is needed depends on the importance of what we are trying to protect. For Example, Y could be a database where we store credit card information. In this case we need to apply all controls needed to secure PCI / DSS data that includes proper segmentation, Encryption, Inspection and so on.
Different transactions may need a different level of security as depicted below, thus this could get very complex to build and manage quickly. Where do I put my controls? Should my inspection be closer to the resource I am trying to protect, or should I use an aggregation later? Should I use some filtering devices closer at the Edge of the network to reduce what needs to be inspected later?
What about my security Policy? Should that be part of my Architecture design? Maybe not from a management perspective but it’s important to understand where we are applying policy and what impact that will have on traffic patterns. For example, return asymmetric traffic often cause problems with firewalls thus it’s best to design placement of your controls properly.
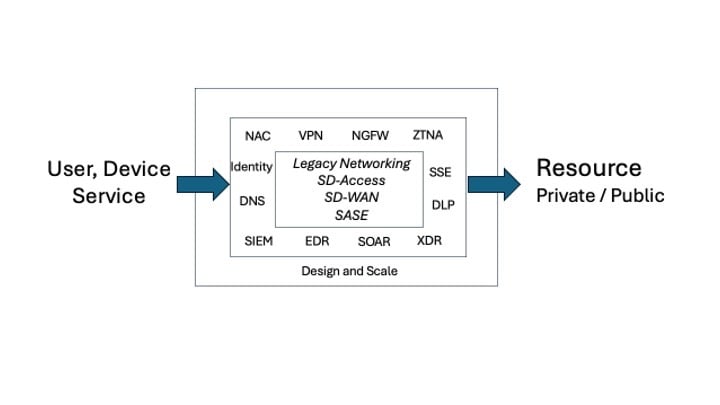
Clearly our job to secure networks has become more complex and more difficult. Here are couple of the areas that come to mind when thinking about designing Secure networks.
Classification: Asset inventory and classification is critical and will be used as basis for constructing policy and for visibility.
Segmentation: Separating networks into VRFs and VLANs will simplify network design and can protect against lateral movement.
Defense in Depth: Multiple levels of defense is critical. NGFW, SSE and other Inspection / enforcement services will be needed especially when accessing applications and critical network segments from on Premise to Cloud.
Least Privilege: Let's only give a user, device access to only what they need access to.
Frameworks: Frameworks like NIST can be used as a great resource to help guide security professionals design network security. They are technology independent and address other key elements such as processes.
In summary the more segmentation and isolation for critical services you have in your network design the better and let’s make sure we apply the right controls along with the right visibility. Understanding and applying failover mechanisms to respond properly in case of a breach or a network problem is also critical. Add policy and governance along with the right processes and you should be on the right path.
For more information on how to better design your network for Security please reach out to Calpean.